29 Jul 2022
Authentication And Authorization Protocols

What is Authentication & Authorization Protocols
The following is an overview reference point to the Authentication & Authorization Protocols, which is what we all use every day to sign into our favourite apps, for work or personal like email or social media & banking.
Authentication is the act of proving an assertion, such as the identity of a computer system user. In contrast with identification, the act of indicating a person or thing's identity, authentication is the process of verifying that identity.
Authorization is the function of specifying access rights/privileges to resources, which is related to general information security and computer security, and to access control in particular. More formally, "to authorize" is to define an access policy.
Ref - Wikipedia
What is OpenID (OIDC) Connect?
OpenID Connect 1.0 is a simple identity layer on top of the OAuth 2.0 protocol. It allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.
OpenID Connect allows clients of all types, including Web-based, mobile, and JavaScript clients, to request and receive information about authenticated sessions and end-users. The specification suite is extensible, allowing participants to use optional features such as encryption of identity data, discovery of OpenID Providers, and session management, when it makes sense for them.
Ref
https://openid.net/connect/
https://en.wikipedia.org/wiki/OpenID
What is SAML Security Assertion Markup Language?
SAML is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider. SAML is an XML-based markup language for security assertions (statements that service providers use to make access-control decisions).
Ref
https://wiki.oasis-open.org/security
https://en.wikipedia.org/wiki/Security_Assertion_Markup_Language
SAML vs. OpenID (OIDC)
SAML (SAML 1.0 and 2.0) and OpenID Connect (OIDC) are identity protocols, designed to authenticate users, and provide identity data for access control and as a communication method for a user’s identity. Either protocol may be the basis for Identity Providers (IdPs) that offer a range of user identity management and services and may be used for single sign-on (SSO) applications.
Ref
https://auth0.com/intro-to-iam/saml-vs-openid-connect-oidc/
OAuth 2.0 vs. OpenID Connect
The first thing to understand is that OAuth 2.0 is an authorization framework, not an authentication protocol. OAuth 2.0 can be used for a lot of cool tasks, one of which is person authentication.
OpenID Connect is a “profile” of OAuth 2.0 specifically designed for attribute release and authentication.
Azure Active Directory integrations with authentication and synchronization protocols
Microsoft Azure Active Directory (Azure AD) enables integration with many authentications and synchronization protocols. The authentication integrations enable you to use Azure AD and its security and management features with little or no changes to your applications that use legacy authentication methods. The synchronization integrations enable you to sync user and group data to Azure AD, and then user Azure AD management capabilities. Some sync patterns also enable automated provisioning.
Legacy authentication protocols
The following table presents authentication Azure AD integration with legacy authentication protocols and their capabilities. Select the name of an authentication protocol to see
- A detailed description
- When to use it
- Architectural diagram
- Explanation of system components
- Links for how to implement the integration
|
Authentication protocol |
Authentication |
Authorization |
Multi-factor Authentication |
Conditional Access |
 |
 |
 |
 |
|
 |
||||
 |
 |
 |
 |
|
 |
 |
 |
 |
|
 |
 |
 |
 |
|
 |
 |
 |
||
 |
 |
 |
 |
|
 |
 |
 |
||
 |
 |
 |
 |
|
 |
 |
 |
 |
Synchronization patterns
The following table presents Azure AD integration with synchronization patterns and their capabilities. Select the name of a pattern to see
- A detailed description
- When to use it
- Architectural diagram
- Explanation of system components
- Links for how to implement the integration
|
Synchronization pattern |
Directory synchronization |
User provisioning |
 |
||
 |
||
 |
 |
OAuth 2.0 authentication with Azure Active Directory
The OAuth 2.0 is the industry protocol for authorization. It allows a user to grant limited access to its protected resources. Designed to work specifically with Hypertext Transfer Protocol (HTTP), OAuth separates the role of the client from the resource owner. The client requests access to the resources controlled by the resource owner and hosted by the resource server. The resource server issues access tokens with the approval of the resource owner. The client uses the access tokens to access the protected resources hosted by the resource server.
OAuth 2.0 is directly related to OpenID Connect (OIDC). Since OIDC is an authentication and authorization layer built on top of OAuth 2.0, it isn't backwards compatible with OAuth 1.0. Azure Active Directory (Azure AD) supports all OAuth 2.0 flows.
Use for: Rich client and modern app scenarios and RESTful web API access.
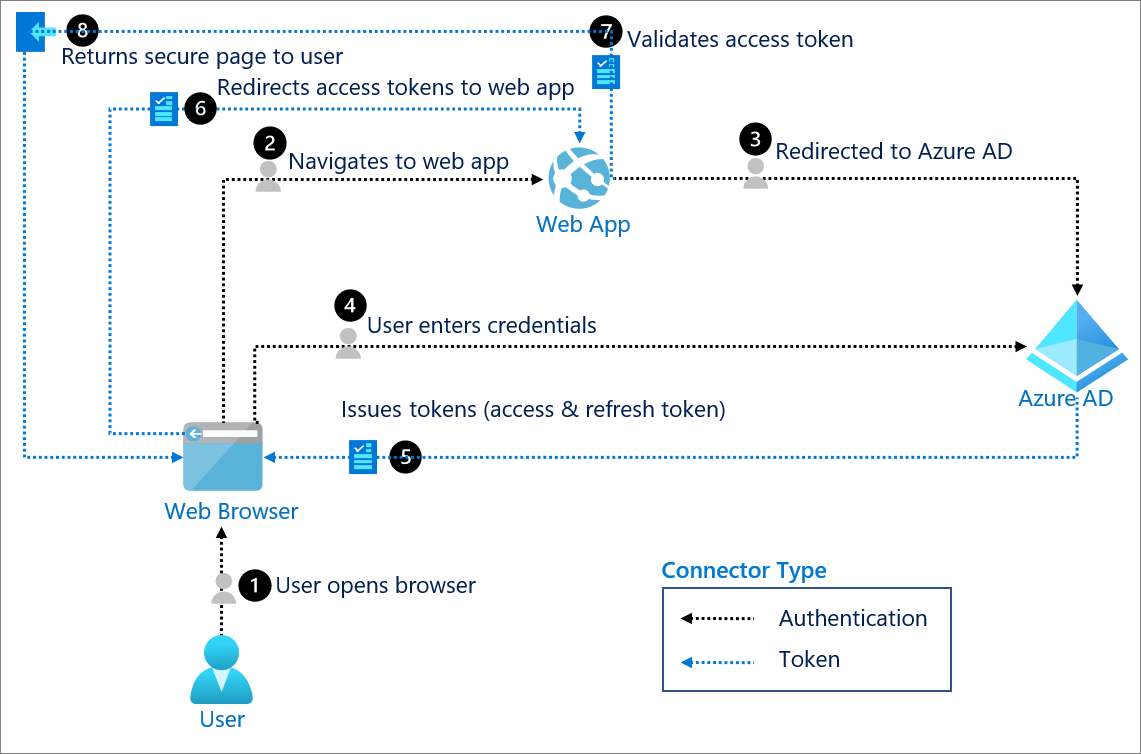
OpenID Connect authentication with Azure Active Directory
OpenID Connect (OIDC) is an authentication protocol based on the OAuth2 protocol (which is used for authorization). OIDC uses the standardized message flows from OAuth2 to provide identity services.
The design goal of OIDC is "making simple things simple and complicated things possible". OIDC lets developers authenticate their users across websites and apps without having to own and manage password files. This provides the app builder with a secure way to verify the identity of the person currently using the browser or native app that is connected to the application.
The authentication of the user must take place at an identity provider where the user's session or credentials will be checked. To do that, you need a trusted agent. Native apps usually launch the system browser for that purpose. Embedded views are considered not trusted since there's nothing to prevent the app from snooping on the user password.
In addition to authentication, the user can be asked for consent. Consent is the user's explicit permission to allow an application to access protected resources. Consent is different from authentication because consent only needs to be provided once for a resource. Consent remains valid until the user or admin manually revokes the grant.
Use when: There is a need for user consent and for web sign in.

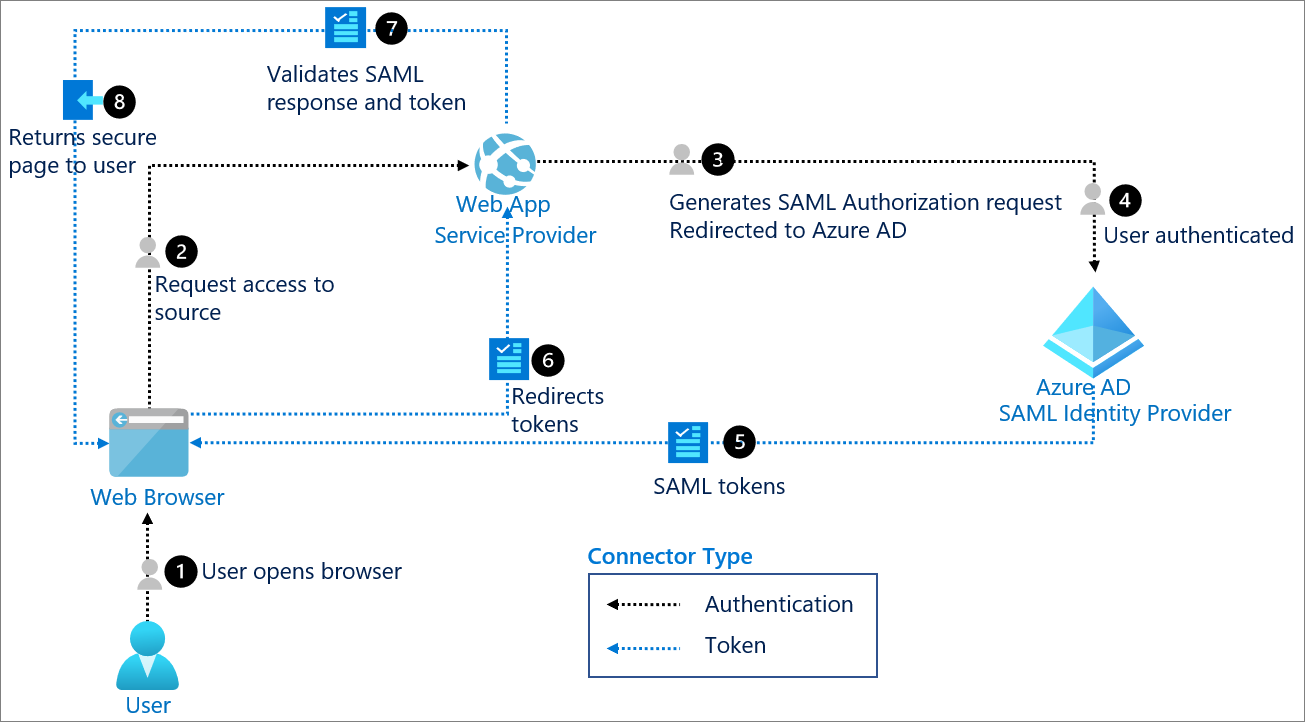
SAML authentication with Azure Active Directory
Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between an identity provider and a service provider. SAML is an XML-based markup language for security assertions, which are statements that service providers use to make access-control decisions.
The SAML specification defines three roles:
- The principal, generally a user
- The identity provider (IdP)
- The service provider (SP)
Use when: There's a need to provide a single sign-on (SSO) experience for an enterprise SAML application.
While one of most important use cases that SAML addresses is SSO, especially by extending SSO across security domains, there are other use cases (called profiles) as well.