05 Apr 2021
Connect Azure Sentinel to AWS CloudTrail
Connect Azure Sentinel to AWS CloudTrail
Use the AWS connector to stream your AWS CloudTrail management events into Azure Sentinel. This connection process delegates access for Azure Sentinel to your AWS resource logs, creating a trust relationship between AWS CloudTrail and Azure Sentinel. This is accomplished on AWS by creating a role that gives permission to Azure Sentinel to access your AWS logs.
Note
AWS CloudTrail has built-in limitations in its LookupEvents API. It allows no more than two transactions per second (TPS) per account, and each query can return a maximum of 50 records. Consequently, if a single tenant constantly generates more than 100 records per second in one region, backlogs and delays in data ingestion will result.
Prerequisites
You must have write permission on the Azure Sentinel workspace.
Note
Azure Sentinel collects CloudTrail management events from all regions. It is recommended that you do not stream events from one region to another.
Connect AWS
-
In Azure Sentinel, select Data connectors and then select the Amazon Web Services line in the table and in the AWS pane to the right, click Open connector page.
-
Follow the instructions under Configuration using the following steps.
-
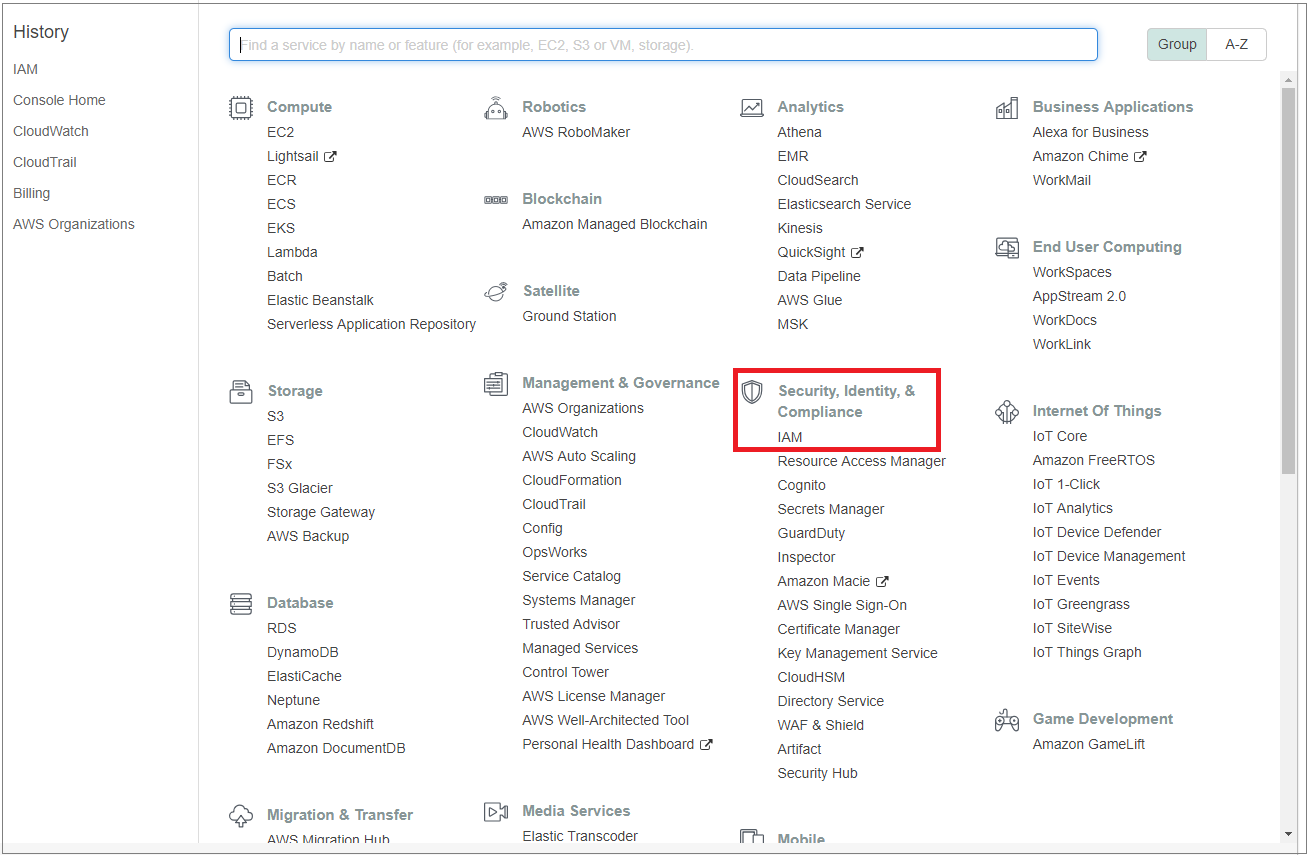
In your Amazon Web Services console, under Security, Identity & Compliance, select IAM.
-
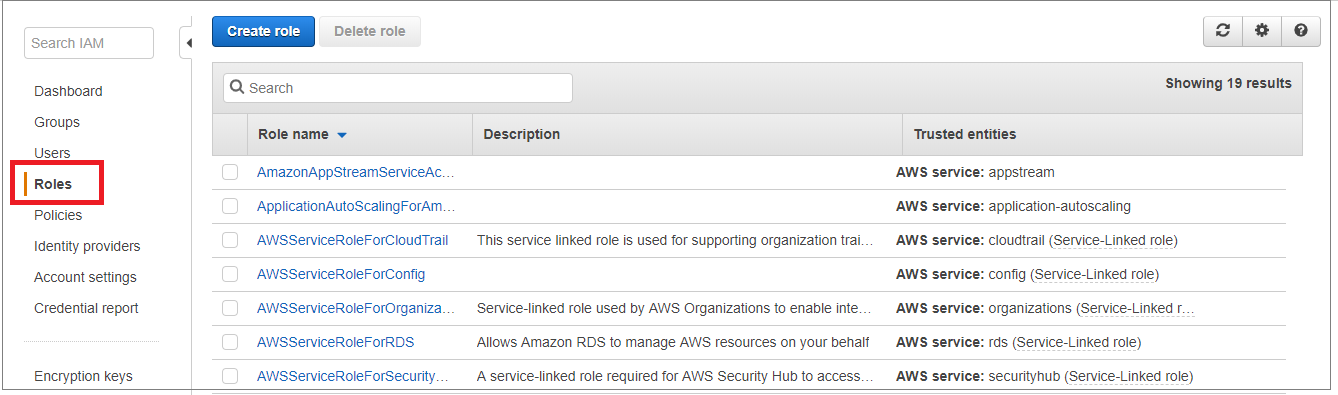
Choose Roles and select Create role.
-
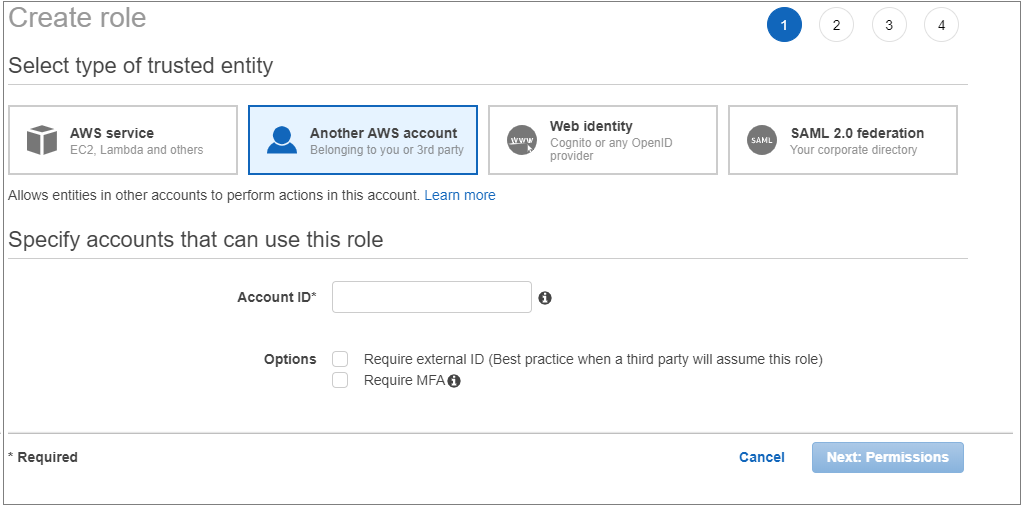
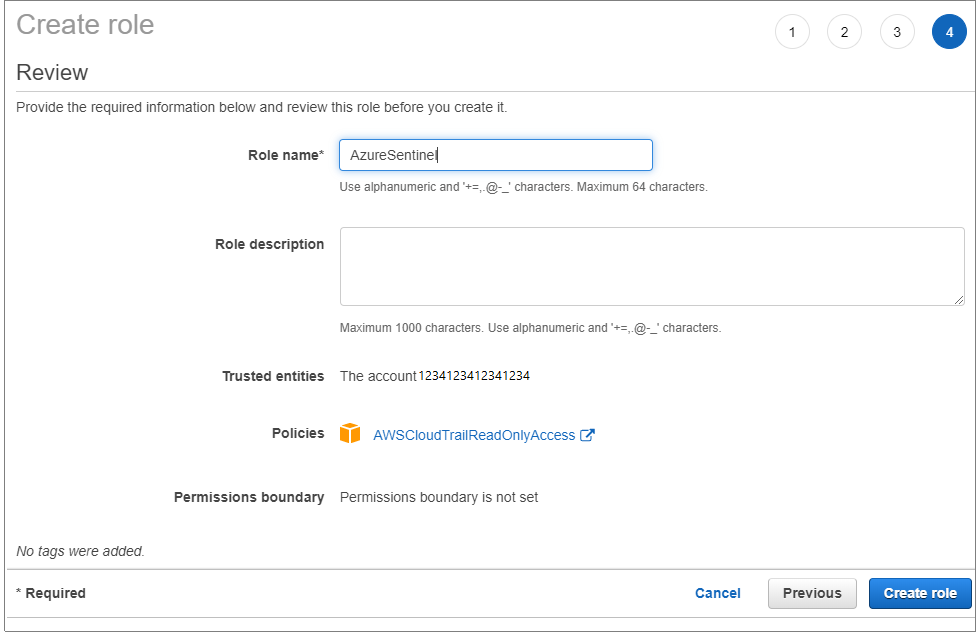
Choose Another AWS account. In the Account ID field, enter the Microsoft Account ID (123412341234) that can be found in the AWS connector page in the Azure Sentinel portal.
-
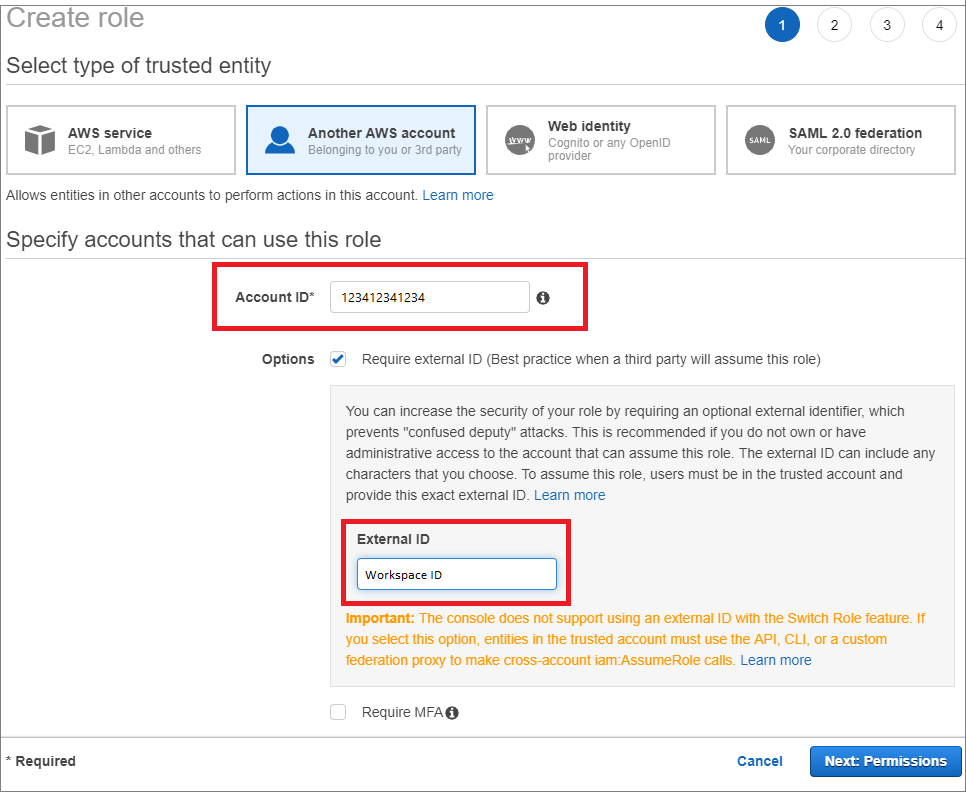
Make sure Require External ID is selected and then and enter the External ID (Workspace ID) that can be found in the AWS connector page in the Azure Sentinel portal.
-
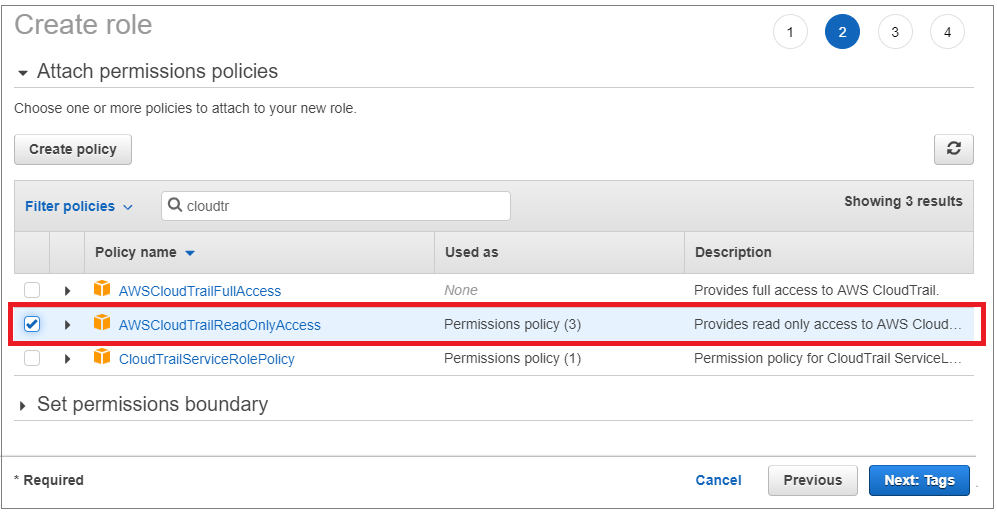
Under Attach permissions policy select AWSCloudTrailReadOnlyAccess.
-
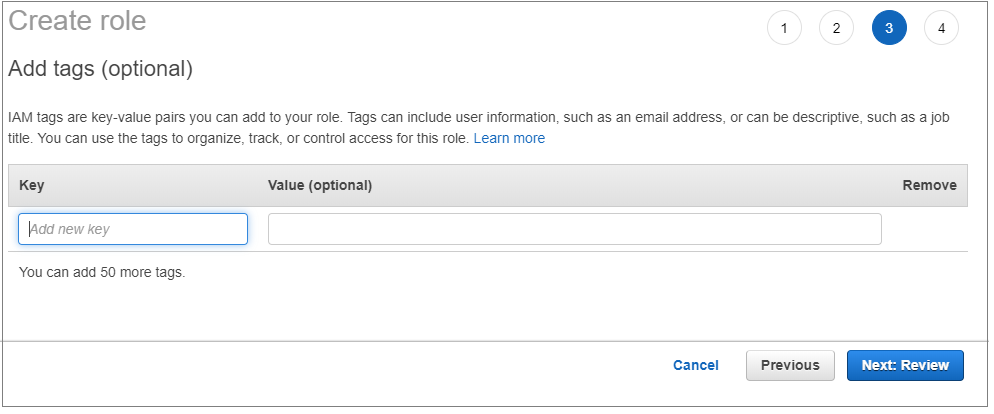
Enter a Tag (Optional).
-
Then, enter a Role name and select the Create role button.
-
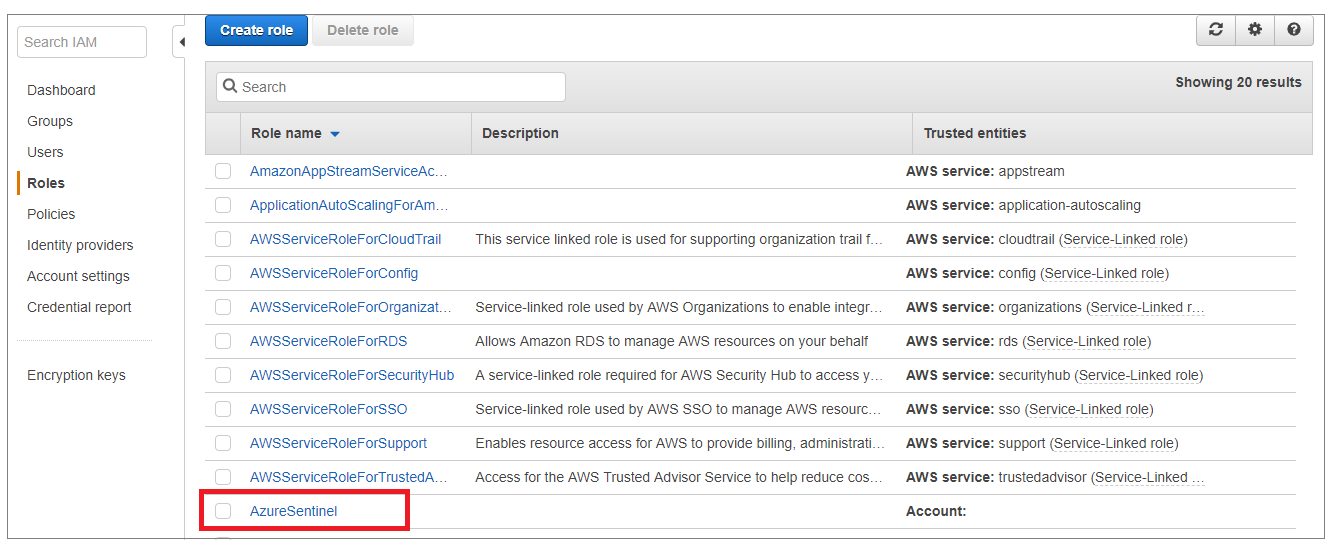
In the Roles list, choose the role you created.
-
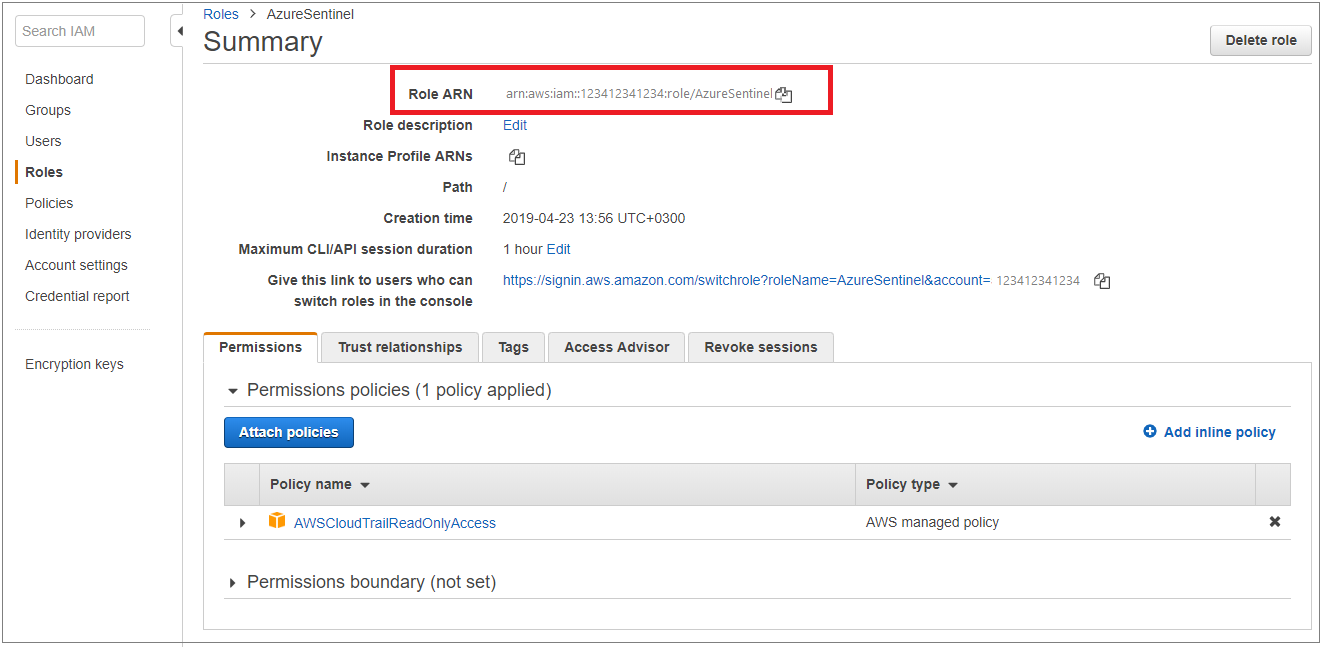
Copy the Role ARN. In the Azure Sentinel portal, in the Amazon Web Services connector screen, paste it into the Role to add field and click Add.
-
To use the relevant schema in Log Analytics for AWS events, search for AWSCloudTrail.
Important
As of December 1, 2020, the AwsRequestId field has been replaced by the AwsRequestId_ field (note the added underscore). The data in the old AwsRequestId field will be preserved through the end of the customer's specified data retention period.