24 Feb 2020
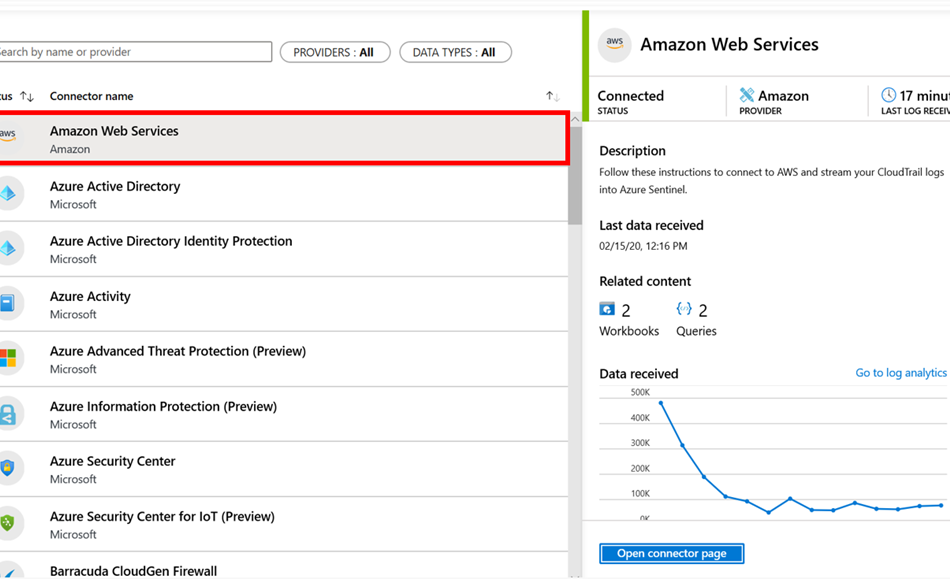
AWS CloudTrail logs - Azure Sentinel
SecOps teams are increasingly challenged to protect assets across distributed environments, analyze the growing volume of security data, and prioritize response to real threats.
As a cloud-native SIEM solution (security information and event management), Azure Sentinel uses artificial intelligence (AI) and automation to help address these challenges. Azure Sentinel empowers SecOps teams to be more efficient and effective at responding to threats in the cloud, on-premises, and beyond.
More than 60 percent of enterprises have a hybrid cloud strategy—a combination of private and multi-cloud deployments. We’re committed to help SecOps teams defend the entire stack, not just Microsoft workloads. That’s why Azure Sentinel includes built-in connectors to bring together data from Microsoft solutions with data from other cloud platforms and security solutions.
New and existing customers of Azure Sentinel can take advantage of this offer by using the built-in connector for AWS CloudTrail logs. Data retention charges after 90 days period and other related charges are applicable during this time as per Azure Sentinel terms. Learn more about Azure Sentinel pricing.
Once connected to your AWS CloudTrail logs, you can visualize and get relevant insights using built-in workbooks. You can even customize these dashboards and combine insights from other sources to meet your needs:
Detections and hunting queries developed by Microsoft Security experts will make it easier to identify and respond to potential threats in your AWS environment:
Gain visibility into threats targeting IoT
With the exponential growth in connected devices creating an uptick in attacks targeting IoT, it is critical for enterprise SecOps teams to include IoT data in their scope. A new Azure Security Center for IoT connector makes it easy for customers to onboard data from Azure IoT Hub-managed deployments into Azure Sentinel. Customers can now monitor alerts across all IoT Hub deployments along with other related alerts in Azure Sentinel, inspect and triage IoT incidents, and run investigations to track an attacker’s lateral movement within their enterprise.
With this announcement Azure Sentinel is the first SIEM with native IoT support, allowing SecOps and analysts to identify threats in these complex converged environments.
In addition, Upstream Security, a cloud-based automotive cybersecurity detection and response company, is launching integration with Azure Sentinel. This will enable customers to send threats detected by Upstream Security’s C4 platform to Azure Sentinel for further investigation.
Collect data from additional data sources
We’re continually adding new data connectors from leading security solutions and partners. Each of these data connectors have sample queries and dashboards to help you start working with the data immediately in Azure Sentinel:
- Forcepoint—Three new connectors enable customers to bring in data from Forcepoint NextGen Firewall logs (NGFW), Cloud Access Security Broker (CASB) logs and events, and Data Loss Prevention (DLP) incident data in Azure Sentinel.
- Zimperium—Customers can use the Zimperium Mobile Threat Defense (MTP) connector to get Zimperium threat logs in Azure Sentinel.
- Squadra technologies—Customers can get their Squadra secRMM (security removable media manager) event data for the USB removable devices in Azure Sentinel.
Bring SIGMA detections to Azure Sentinel
The SOC Prime Threat Detection Marketplace—which includes 950+ rules mapped to MITRE ATT&CK to address over 180 attacker techniques—now supports Azure Sentinel analytics rules. The SOC Prime marketplace provides unprecedented access to the latest threat detection content from the SIGMA community, SOC Prime team, and its Threat Bounty Program members. New detection rules are continuously created and updated by security researchers and published daily at the SOC Prime marketplace, helping companies to detect latest threats, vulnerability exploitation attempts and enable TTP-based threat hunting. Once the rules are published, using the Azure Sentinel integration you can instantly deploy them from within TDM to your Azure Sentinel instance with just one click.
Use ReversingLabs threat intelligence to inform threat response
ReversingLabs brings two new integrations to Azure Sentinel, enabling customers to leverage rich ReversingLabs threat intelligence for hunting and investigation in Azure Sentinel. The first integration features an Azure Sentinel Notebooks sample that connects to the Reversing Labs API to enable hunting scenarios that include ReversingLabs threat intelligence data. In addition, a new ReversingLabs TitaniumCloud connector for Azure Logic Apps and sample playbook enable security incident responders to automatically identify key information about file-based threats to rapidly triage incoming alerts.
Detect threats with greater confidence using new machine learning models
Azure Sentinel uses AI-based Fusion technology to stitch together huge volumes of low and medium fidelity alerts across different sources and then elevates the combined incidents to a high priority alert that security professionals can investigate. Learn how Azure Sentinel evaluated nearly 50 billion suspicious signals for Microsoft in a single month to create just 25 high confidence incidents for our SecOps team to investigate.
In addition to the existing machine learning detections that look for multi-stage attacks, we are introducing several new scenarios in public preview using Microsoft Defender Advanced Threat Protection (ATP) and Palo Alto logs. These new detections will help SecOps teams to identify attacks that may otherwise be missed and reduce the mean time to remediate threats.
Manage incidents across multiple tenants and workspaces
Managed security service providers and large enterprises often need a central place to manage security incidents across multiple workspaces and tenants. Integration of Azure Sentinel with Azure Lighthouse now lets you view and investigate incidents from different tenants and workspaces in a central pane. This will also help enterprises who need to keep separate workspaces in different regions to meet regulatory requirements while managing incidents in a central place.
Join the Azure Sentinel private preview in Azure Government
Azure Sentinel is now available in private preview in Azure Government, starting with US Gov Virginia region. To join the preview please contact us at sentinelazuregov@microsoft.com.
Azure Sentinel is currently going through the FedRAMP-High certification process, and Microsoft anticipates achieving compliance by the summer of 2020.